
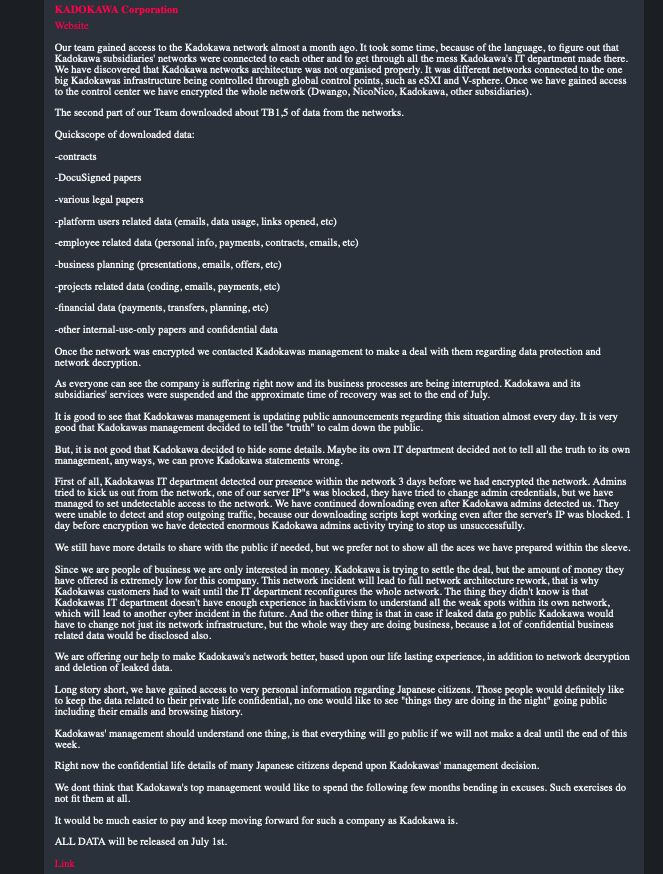
A hacking group generally known as BlackSuit has claimed accountability for the latest ransomware assault on publishing big Kadokawa Threatened to launch stolen knowledge if ransom isn’t paid by July 1, 2024.
BlackSuit is a infamous ransomware gang that emerged as a rebrand of the Royal ransomware operation. The group is believed to have ties to the now defunct cybercrime syndicate Conti, a serious participant within the ransomware panorama.
Whereas the precise location and identification of the members are nonetheless unclear, cybersecurity specialists have discovered a number of indicators pointing to ties to Russia.
Kadokawa first acknowledged the cyberattack in early June, reporting disruptions to a number of web sites and companies. Since then, the corporate has offered common updates on its efforts to revive techniques and examine the incident.
Nevertheless, BlackSuit’s reported assertion on June 27, 2024 revealed the total extent of the breachclaiming that 1.5 terabytes of delicate data was stolen, together with enterprise plans, person credentials, contracts and monetary knowledge.
BlackSuit claims to have exploited vulnerabilities in Kadokawa’s community structure and gained entry to a “management heart” that allowed them to encrypt the whole community, affecting a number of subsidiaries together with Dwango and NicoNico.
Regardless of Kadokawa’s IT division noticing their presence, the hackers have been capable of proceed downloading knowledge for a number of days earlier than encrypting the community.
The hacking group claims that Kadokawa is negotiating a deal however has supplied an “extraordinarily low” ransom for an organization of its dimension. They warned that the leaked knowledge may have important penalties for Kadokawa’s enterprise operations and the privateness of many Japanese residents.
The ransom isn’t specified within the assertion. View the picture of the assertion under.
In the newest replaceKadokawa assured clients that no bank card data was compromised because it was not saved on their system.
The corporate additionally said that its prime priorities have been to revive accounting features and normalize manufacturing and distribution in its publishing enterprise, with outcomes anticipated in early July.
Whereas the manufacturing of latest publications stays steady, the cargo of present publications is at the moment at one-third of regular ranges. To mitigate the impression, Kadokawa is implementing different preparations, together with growing human assets.
Within the Net Providers enterprise, all Niconico household companies stay suspended, though interim companies resembling Niconico Video (Re:tmp) and Niconico Stay Streaming (Re:tmp) have been delivered.
Present companies resembling Niconico Manga smartphone model and NicoFT have additionally resumed.
The Merchandise enterprise has seen restricted impression, with delivery features functioning usually. Nevertheless, the failure of Kadokawa’s account authentication perform has prevented customers from logging into sure on-line shops.
Momentary pages have been created for affected customers. Kadokawa revealed that they are going to proceed to replace on this difficulty.



